ALL IN ONE MEGA PACK INCLUDES:
Cyber Security Financial Model/Business Plan Excel Template
Pitch Deck Template For PowerPoint, Keynote & Google Slides
Business Plan Guide and Business Plan Template in MS Word Format
Financial Dashboard in Excel To Track Your Business Performance
Cyber Security Startup Budget Info
Highlights
When it comes to cybersecurity risk assessment, it is important to have a solid framework in place for managing potential risks. This includes allocating a budget specifically for cybersecurity measures, conducting cost benefit analyses to determine the financial impact of cyber attacks, estimating breach costs, and creating a cybersecurity incident response plan. It is also important to have a compliance framework in place and to consider the organization's cybersecurity risk appetite in the risk mitigation strategy. Additionally, a cybersecurity maturity model, such as the NIST Cybersecurity Framework, can help guide the organization in determining their current cybersecurity status and areas for improvement. Threat modeling can also assist in identifying potential risks and vulnerabilities. Ultimately, investing in a strong cybersecurity program can have a positive return on investment and help protect the organization from costly cybersecurity breaches.
Cybersecurity risk assessment methodology and framework have become a critical aspect of businesses. The financial impact of cyber attacks has driven companies to allocate cybersecurity budgets to mitigate potential losses. A cybersecurity cost benefit analysis and return on investment can help companies determine the value of their cybersecurity initiatives. A cybersecurity breach cost estimation and incident response plan should be incorporated into a compliance and governance framework that aligns with the cybersecurity risk appetite. The cybersecurity maturity model and threat modeling can improve the risk mitigation strategy. Using a cybersecurity financial model excel template can aid in identifying drivers for profitability and loss, forecasting sales, and planning for liquidity and valuation.
Description
Our cybersecurity financial modeling template is a comprehensive tool that allows businesses to analyze the financial impact of cyber attacks and allocate their cybersecurity budget effectively. With this model, businesses can perform a cost-benefit analysis and calculate the return on investment for cybersecurity measures. It also includes a cybersecurity risk assessment methodology, risk appetite, and a risk management framework. The template provides a cybersecurity breach cost estimation and a cybersecurity incident response plan. Additionally, it offers compliance and governance frameworks, maturity models, and cybersecurity threat modeling. By utilizing this tool, businesses can make informed decisions and secure their systems against cyber threats.Cyber Security Financial Plan Reports
All in One Place
Managing cybersecurity risks is essential for businesses today. A cybersecurity risk assessment model helps identify potential threats and vulnerabilities, while cybersecurity cost benefit analysis and return on investment models aid in allocating budgets. A cybersecurity risk management framework outlines strategies for risk mitigation, and a compliance framework ensures that legal requirements are met. A breach cost estimation and incident response plan are vital to handle cyber incidents. More mature cybersecurity governance and risk mitigation strategies can be achieved through a cybersecurity maturity model with threat modeling and a risk assessment methodology. A cybersecurity risk appetite sets the organizational tolerance for risk.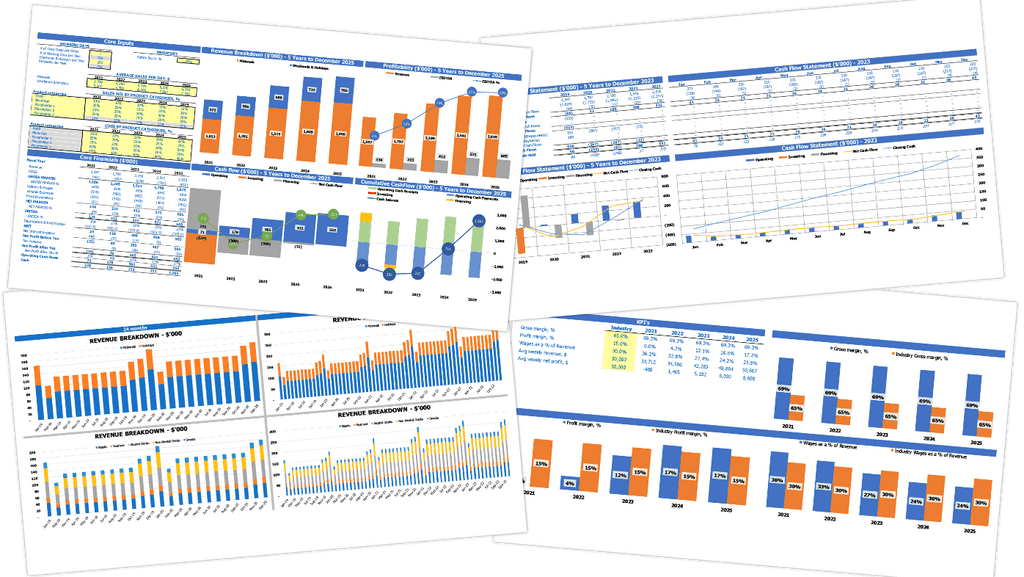
Dashboard
Effective cybersecurity requires a comprehensive approach, from cybersecurity governance to implementing a cybersecurity risk assessment methodology. A cybersecurity risk assessment model can identify potential vulnerabilities and estimate the financial impact of cyber attacks. Using a cybersecurity cost benefit analysis and cybersecurity breach cost estimation, organizations can allocate their cybersecurity budget effectively. A cybersecurity risk management framework and incident response plan can mitigate cybersecurity risk, and a cybersecurity compliance framework and maturity model can help organizations establish their cybersecurity risk appetite and formulate cybersecurity risk mitigation strategies. Threat modeling is also essential in identifying and addressing potential cybersecurity risks.
Business Financial Statement Template
Cybersecurity risk management is crucial for any organization's security posture. To effectively assess and mitigate risks in a cost-effective manner, organizations need to use a cybersecurity risk assessment model and methodology. This allows them to estimate the financial impact of cyber attacks and allocate an appropriate cybersecurity budget. A cybersecurity governance framework, compliance framework, and incident response plan are essential components of a strong cybersecurity posture. A cybersecurity cost-benefit analysis and return on investment analysis can help organizations make informed decisions about their cybersecurity investments. Threat modeling and a cybersecurity risk appetite are crucial for developing a cybersecurity risk mitigation strategy. A cybersecurity maturity model can help organizations measure their progress towards achieving a more effective cybersecurity posture.
Sources And Uses Chart
To ensure the security of your business, it's essential to establish a comprehensive cybersecurity risk assessment methodology. By determining your cybersecurity risk appetite, you can make informed decisions about cybersecurity budget allocation and develop a cybersecurity risk management framework. A cybersecurity governance framework and compliance framework can also be incredibly useful. You can estimate the financial impact of cyber attacks and develop a cybersecurity cost benefit analysis to determine the ROI of your security measures. A cybersecurity maturity model can help track improvements, while a cybersecurity breach cost estimation and incident response plan can mitigate damage. Finally, employ a cybersecurity threat modeling.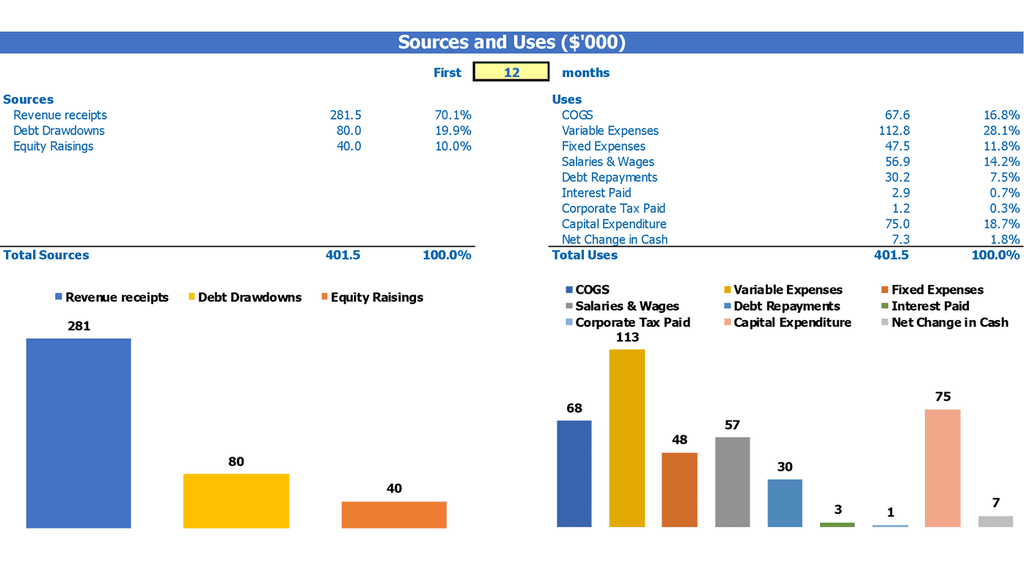
Break Even Calculation
Using various cybersecurity frameworks and models, such as cybersecurity risk assessment methodology, threat modeling, compliance, and governance frameworks, businesses can determine their cybersecurity risk appetite and develop a risk management strategy accordingly. To effectively allocate cybersecurity budgets, companies need to conduct a cost-benefit analysis and estimate the financial impact of cyber attacks by creating breach cost estimations. Additionally, companies need to have an incident response plan in place to mitigate the effects of a breach, and utilize maturity models to assess their cybersecurity readiness. Ultimately, cybersecurity ROI can be improved by aligning cybersecurity investments with business objectives.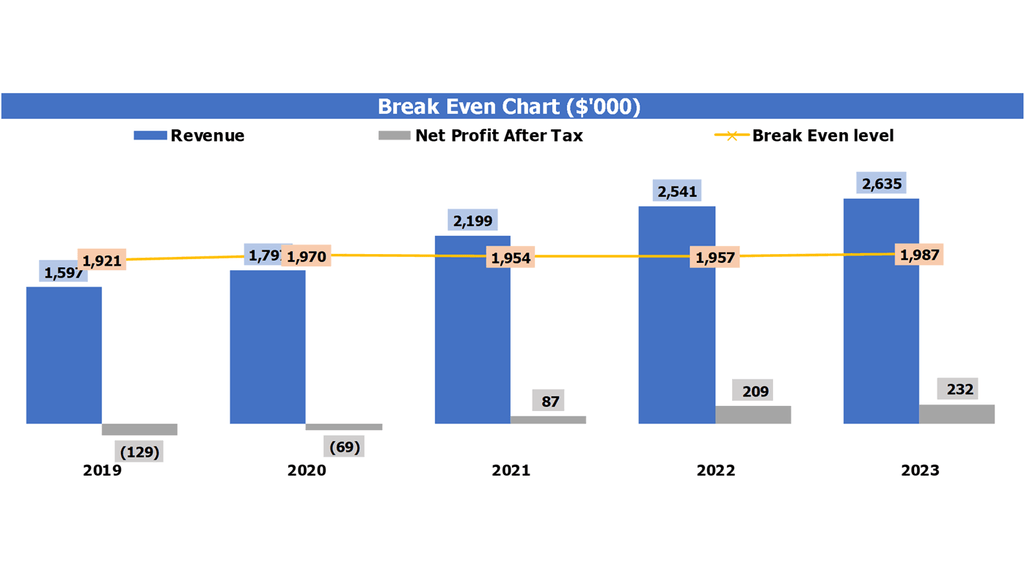
Top Revenue
Building a robust cybersecurity strategy requires a comprehensive understanding of potential risks and financial impacts. This includes using advanced cybersecurity risk assessment models and methodologies, as well as implementing strong cybersecurity risk management and governance frameworks. It's equally important to conduct regular cost-benefit analyses and breach cost estimations to allocate budgets effectively and maximize return on investment. Developing cybersecurity incident response plans and ensuring compliance with regulatory frameworks can further enhance an organization's protection against threats. A strong cybersecurity risk mitigation strategy and risk appetite, informed by threat modeling, can help businesses stay one step ahead of evolving threats.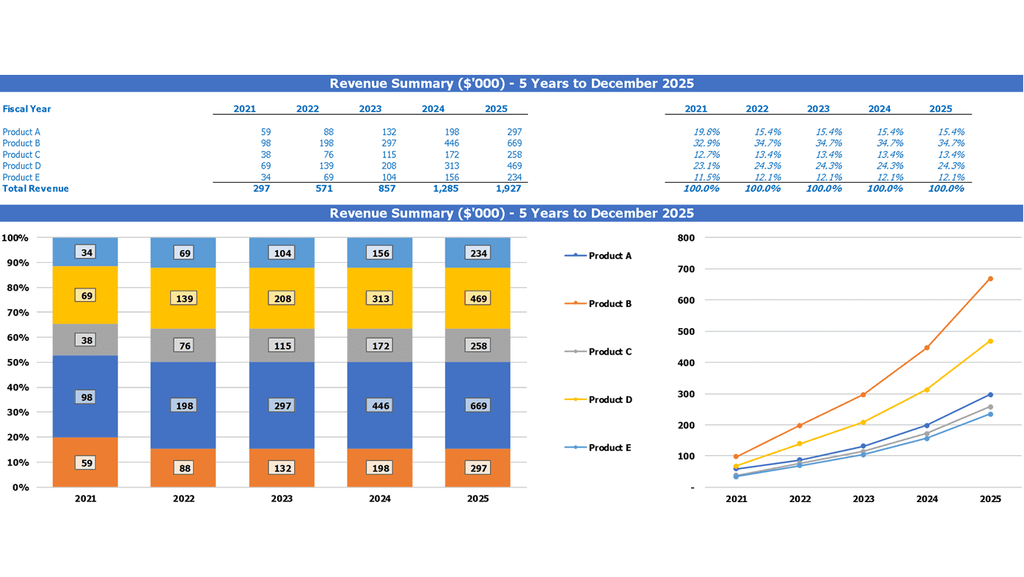
Company Top Expenses List
Effective cybersecurity risk management requires a careful and methodical approach. To begin, companies should engage in a thorough cybersecurity risk assessment using a proven methodology and model. This should be followed by the development of a cybersecurity risk management framework, including clear policies, procedures, and guidelines. To ensure that cybersecurity receives the necessary funds, companies should perform a cost benefit analysis and allocate resources according to the potential financial impact of cyber attacks. Additionally, a cybersecurity governance and compliance framework should be in place, as well as an incident response plan and mitigation strategy. Ongoing monitoring and measurement of cybersecurity maturity and risk appetite are also vital to maintaining a secure enterprise.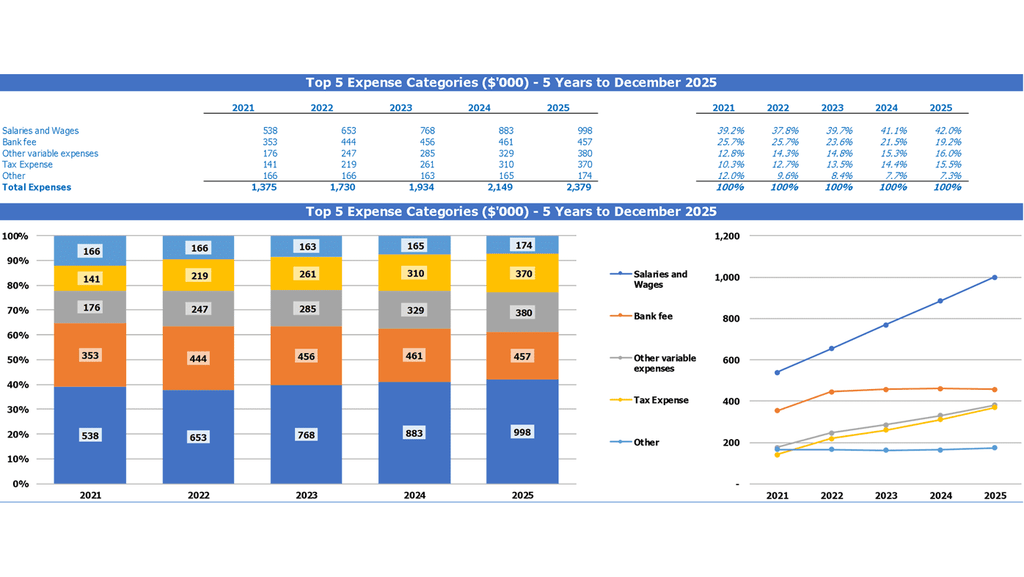
Cyber Security Financial Projection Expenses
Costs
Ensure your business is protected from potential cyber attacks with our cybersecurity risk assessment model. Our cybersecurity cost benefit analysis will help with budget allocation, while our cybersecurity risk management framework will minimize financial impact. Our cybersecurity breach cost estimation and incident response plan will prepare you for worst-case scenarios, and our compliance and governance frameworks will ensure adherence to industry standards. Use our cybersecurity maturity model and risk appetite assessment to develop a comprehensive cybersecurity risk mitigation strategy. Our threat modeling methodology will identify potential vulnerabilities, while our cybersecurity return on investment analysis will ensure a positive impact on your bottom line.
Capital Budgeting Analysis
Investing in cybersecurity can prove beneficial for businesses in the long run. By implementing a cybersecurity risk management framework and conducting regular cybersecurity risk assessments using methodologies like cybersecurity threat modeling, businesses can determine their cybersecurity risk appetite and identify potential security threats. A cost-benefit analysis and estimating the financial impact of cyber attacks can aid in allocating a proper cybersecurity budget. Developing a cybersecurity incident response plan and complying with cybersecurity frameworks like cybersecurity governance and compliance framework, can further strengthen a business's cybersecurity posture. Using a cybersecurity maturity model and implementing a cybersecurity risk mitigation strategy can improve the cybersecurity return on investment.
Loan opt-in
Our cybersecurity solutions aim to address the increasing financial impact of cyber attacks through our comprehensive cybersecurity risk assessment methodology, cybersecurity risk management framework, and cybersecurity cost benefit analysis. With our cybersecurity breach cost estimation and cybersecurity incident response plan, we can help you identify vulnerabilities in your organization's cybersecurity governance framework and build a robust cybersecurity risk mitigation strategy. Our cybersecurity maturity model and cybersecurity risk appetite approach can help you allocate your cybersecurity budget effectively while complying with cybersecurity compliance frameworks. Additionally, we provide cybersecurity threat modeling to further enhance your security posture.
Cyber Security Income Statement Metrics
Performance KPIs
Effective cybersecurity requires a thorough understanding of the organization's cyber risk exposure. A cybersecurity risk assessment model can be used to identify potential threats, vulnerabilities, and impact on operations. A cybersecurity risk management framework and incident response plan can be developed based on this model. To ensure proper budget allocation, a cost-benefit analysis and breach cost estimation can be conducted. A cybersecurity compliance and governance framework can also be implemented. Risk appetite and mitigation strategies should be determined using a cybersecurity risk assessment methodology and threat modeling. Ultimately, a return on investment can be achieved by investing in cybersecurity measures to protect against the financial impact of cyber attacks.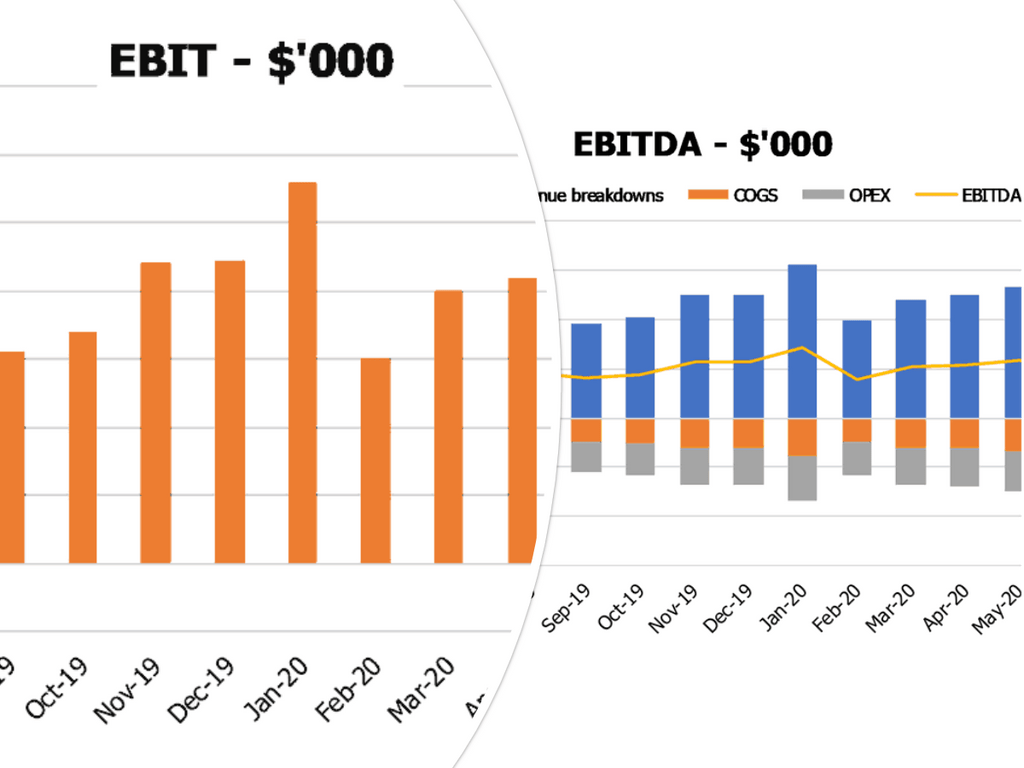
Pro Forma Cash Flow Statement Template
Effective cybersecurity requires a similar approach, using a cybersecurity risk assessment methodology and cybersecurity risk management framework. This includes implementing a cybersecurity governance framework, cybersecurity compliance framework, and cybersecurity incident response plan. It's important to understand the financial impact of cyber attacks through cybersecurity breach cost estimation and conducting a cybersecurity cost benefit analysis. To allocate cybersecurity budget effectively, it's important to consider cybersecurity return on investment. Using a cybersecurity maturity model, cybersecurity risk appetite, and cybersecurity risk mitigation strategy, businesses can develop a sophisticated cybersecurity threat modeling system to stay protected.
Industry Benchmarks
A thorough cybersecurity risk assessment methodology is essential to accurately estimate the financial impact of cyber attacks, allocate a cybersecurity budget, and implement a cybersecurity risk management framework. Performing a cybersecurity cost benefit analysis and calculating the cybersecurity return on investment can also aid in decision-making. It's crucial to have a cybersecurity breach cost estimation, incident response plan, and compliance framework in place, as well as a cybersecurity governance framework and maturity model. Additionally, identifying cybersecurity risk appetite and developing a cybersecurity risk mitigation strategy, including threat modeling, will help protect against cyber threats.
Monthly Profit And Loss Template Excel
The cybersecurity risk assessment model is an essential tool for organizations to measure the potential financial impact of cyber attacks. This, in turn, can determine the necessary budget allocation and guide building a cybersecurity risk management framework. Conducting cybersecurity cost benefit analysis helps calculate the return on investment while preparing cybersecurity breach cost estimation. Furthermore, having a cybersecurity incident response plan in place is crucial for quick, efficient recovery. Creating a cybersecurity compliance framework, governance framework, and using a cybersecurity maturity model with a risk appetite and risk mitigation strategy are key in implementing a cybersecurity risk assessment methodology and threat modeling.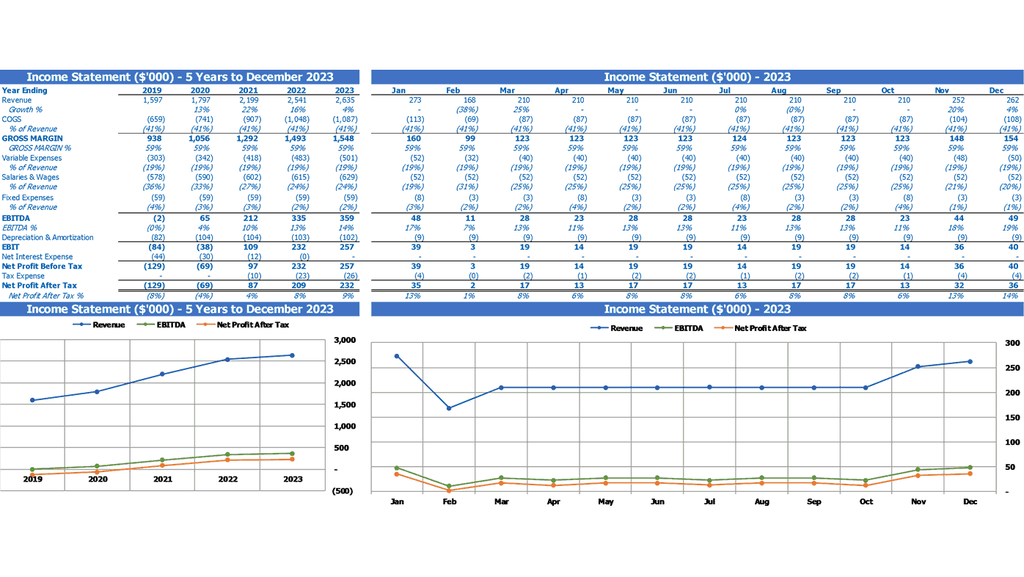
Projected Balance Sheet For 5 Years In Excel Format
Implementing a comprehensive cybersecurity program requires a strategic approach. A cybersecurity risk assessment model helps identify potential threats and calculate the financial impact of cyber attacks. This information can then be used to allocate a cybersecurity budget and develop a risk management framework that includes incident response plans, compliance and governance frameworks, and a risk mitigation strategy. It's also important to consider a cost-benefit analysis and return on investment for cybersecurity measures. Cybersecurity maturity models, risk appetite, risk assessment methodologies, and threat modeling should all be considered to strengthen the overall cybersecurity posture of a company.
Cyber Security Income Statement Valuation
Startup Valuation
This all-in-one cybersecurity financial model simplifies the data calculation needed for investor presentations. It includes pre-built financial templates such as cybersecurity breach cost estimation, cybersecurity compliance framework, and cybersecurity return on investment, among many others. Use our cybersecurity cost benefit analysis and cybersecurity risk assessment methodology to allocate your cybersecurity budget efficiently. Our cybersecurity risk management framework, cybersecurity maturity model, cybersecurity governance framework, and cybersecurity threat modeling tools assist in protecting your business from cyber threats. Lastly, create a cybersecurity incident response plan and set a cybersecurity risk appetite to mitigate potential damages.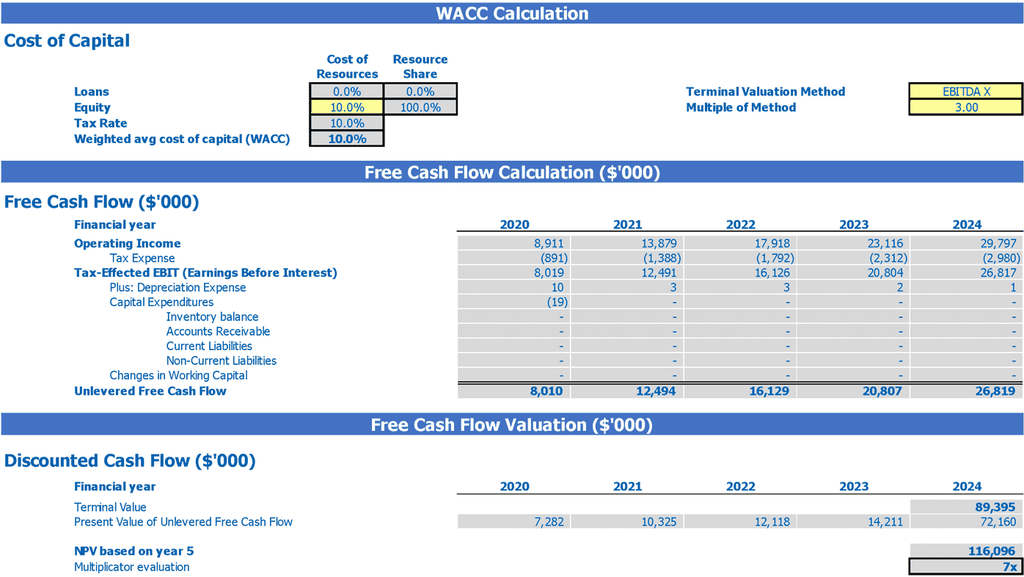
Cap Table For Startups
Effective cybersecurity requires a variety of tools and strategies, from risk assessment models to comprehensive incident response plans. Companies must also consider the financial impact of cyber attacks and allocate budget accordingly. It is important to conduct a cost-benefit analysis and assess return on investment for cybersecurity measures. A strong cybersecurity framework includes governance and compliance components and must be constantly updated as the threat landscape evolves. A mature cybersecurity program includes risk mitigation strategies and threat modeling to ensure the organization's risk appetite is aligned with its overall security goals. Finally, breach cost estimation is critical for planning and budgeting purposes.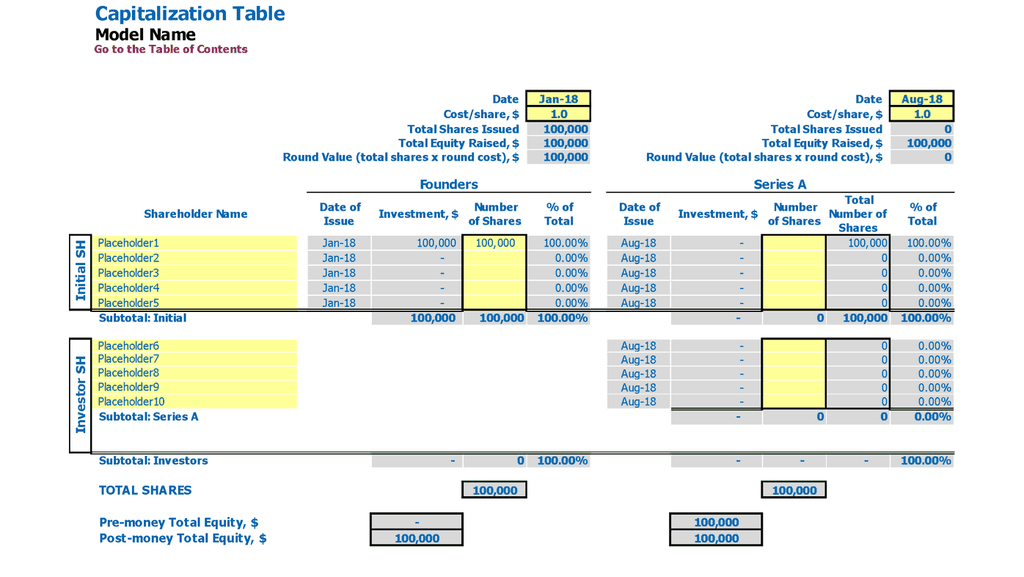
Cyber Security Startup Costs Template Key Features
Predict the Influence of Upcoming Changes
Utilize a cybersecurity risk assessment model to allocate budget and create a risk management framework that includes cost benefit analysis, breach cost estimation, and incident response plans.
Generate growth inspiration
Use a cybersecurity risk assessment model to determine the financial impact of cyber attacks and allocate your cybersecurity budget accordingly.
Simple-to-use
Achieve reliable cybersecurity financial planning with minimal experience and basic Excel skills using our sophisticated model.
Track your spending and staying within budget
Maximize cybersecurity ROI with a comprehensive risk assessment model, cost-benefit analysis, and incident response plan.
Build your plan and pitch for funding
Present a comprehensive cybersecurity risk management plan to ensure financial stability and compliance.
Cyber Security Financial Model Template For Startup Advantages
Using a cybersecurity risk assessment model can aid in developing a cybersecurity budget allocation based on the financial impact of cyber attacks.
Assess and manage cybersecurity risks with a comprehensive framework and budget allocation strategy.
Maximize cyber defense investments with an Excel-based cybersecurity financial model.
Use a cybersecurity risk assessment methodology to calculate the financial impact of cyber attacks and allocate your cybersecurity budget accordingly.
Using a cybersecurity risk assessment methodology can aid in creating a cost-effective cybersecurity budget allocation.


